
|
Date Reported: 14th January 2012  |
Risk Level: MEDIUM-HIGH  |
|
| |
 |
 |
| |
Email Subject: |
(Enhanced Security) Ownership Verification Processing |
|
Apparent Sender: |
Santander Bank Plc  |
|
Return Address: |
onlinesecurity@santander.co.uk  |
|
| Email Format: |
HTML  |
| |
URL of Web Content: |
http://compostera.cl/wp-admin/Redirect.php
 |
|
Anchor text of URLs: |
1)
https://retail.santander.co.uk/LOGSUK_NS_ENS/
BtoChannelDriver.ssobto?dse_operationName=LOG
ON  |
|
Location: |
FT. LAUDERDALE, FLORIDA, UNITED STATES  |
| |
Scam number: |
19627-316925-694260 |
| |
Comments: |
- Email asks you to confirm/update/verify your account data at Santander Bank Plc by visiting the given link. You will be taken to a spoof website where your details will be captured for the phishers.
- Santander Bank Plc never send their users emails requesting personal details in this way.
- The anchor text appears as a legitimate URL, but don't be fooled - clicking on it will take you to a phishing site!
|
| |
|
|
 |
 |
| |
|
| |
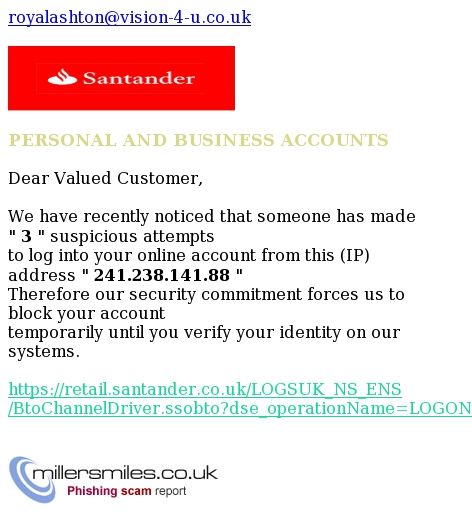
New Page 1
PERSONAL AND BUSINESS ACCOUNTS
Dear Valued Customer,
We have recently noticed that someone has
made " 3 " suspicious attempts
to log into your online account from this
(IP) address " 241.238.141.88 "
Therefore our security commitment forces us
to block your account
temporarily until you verify your identity
on our systems.
https://retail.santander.co.uk/LOGSUK_NS_ENS/
BtoChannelDriver.ssobto?dse_operationName=LOG
ON
...
|
|
Click for full size image |
| |
| Website: |
|
|
| |
|

Click for full size image |