
|
Date Reported: 2nd October 2010  |
Risk Level: MEDIUM-HIGH  |
|
| |
 |
 |
| |
Email Subject: |
Message Update:- Dear Customer |
|
Apparent Sender: |
National Westminister Bank Plc  |
|
Return Address: |
internetbanking@natwestbank.com  |
|
| Email Format: |
HTML  |
| |
URL of Web Content: |
http://udantika.com/css/Login1.php
 |
|
Anchor text of URLs: |
1)
http://www.natwest.com/personal.ashx/Verify,
2) http://udantika.com/css/Login1.php  |
|
Location: |
Location not available  |
| |
Scam number: |
13108-179791-447024 |
| |
Comments: |
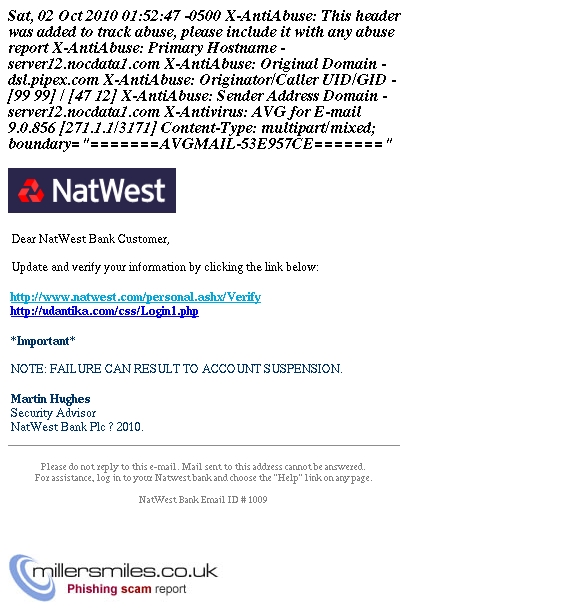
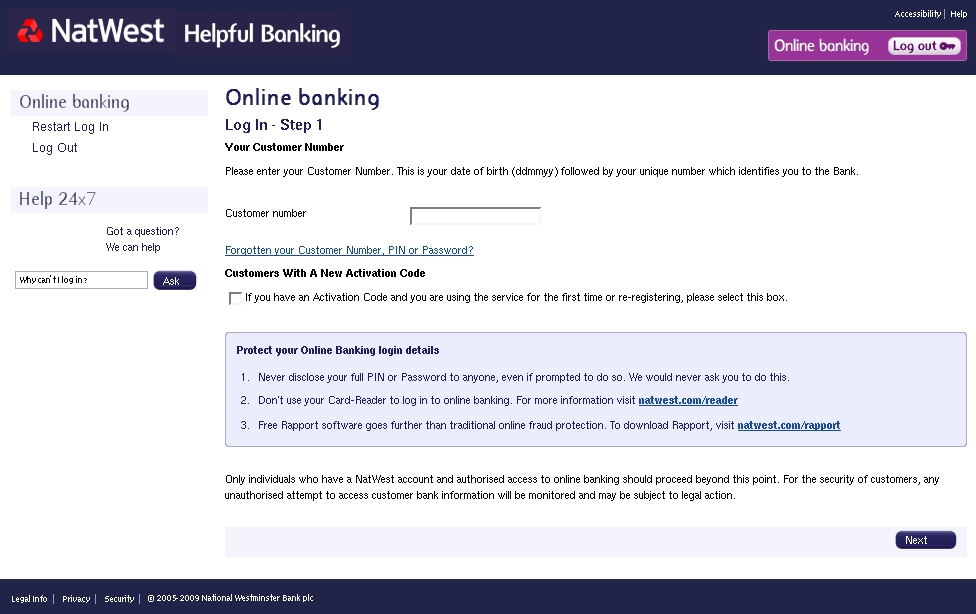
- Email asks you to confirm/update/verify your account data at National Westminister Bank Plc by visiting the given link. You will be taken to a spoof website where your details will be captured for the phishers.
- National Westminister Bank Plc never send their users emails requesting personal details in this way.
- The anchor text appears as a legitimate URL, but don't be fooled - clicking on it will take you to a phishing site!
|
| |
|
|
 |
 |
| |
|
| |
X-ANTIABUSE: This header was added to
track abuse, please include it with any abuse
report
X-ANTIABUSE: Primary Hostname -
server12.nocdata1.com
X-ANTIABUSE: Original Domain -
dsl.pipex.com
X-ANTIABUSE: Originator/Caller UID/GID -
[99 99] / [47 12]
X-ANTIABUSE: Sender Address Domain -
server12.nocdata1.com
X-ANTIVIRUS: AVG for E-mail 9.0.856
[271.1.1/3171]
CONTENT-TYPE: multipart/mixed;
boundary="=======AVGMAIL-53E957CE=======".
|
|
Click for full size image |
| |
| Website: |
|
|
| |
|
Click for full size image |