Another case of Address Bar Spoofing targets
Paypal users with this complex forgery...
This email is very similar to our other recent example
of a Paypal Phishing Scam which involves a complex method of coding and scripting
using HTA, HTML and javascript to deliver a bogus web page which could easily
be mistaken for a genuine paypal.com page.
Clicking that link in the email (which is HTML coded
to look like it will lead to a genuine paypal.com page - https://www.paypal.com/fraudcheck/secure/bill.html?sl=070304)
will trigger a sequence of browser windows...
1. the link in a spoofed email opens
a new browser window which is scripted to immediately close itself and reopen
with the address and status bar removed,
2. this new window further
uses a combination of HTA, HTML and javascript commands to rebuild a fake
address bar using images and text. The text fraudulently displays a genuine
URL - https://www.paypal.com/cgi-bin/webscr?cmd=_login-run, but the true URL
is http://smba.swu.ac.kr/css/.accVerify/secure/log1.htm, which resolves to Seoul
Womens University in Korea.
3. Any data submitted into the forged
Paypal form is forwarded to the fraudsters' email address - broker@easynet.ro
(which resolves to a Global One Communications in Romania) via a script located
on the same server.
If you have received this email, please remember that it is very
common for these email scams to be redistributed at a later date with only slightly
different content or the same but with the fake page(s) hosted by a different
provider. Also, once you have received one of these hoaxes, it is also common
place to receive at least another one and usually a day or two after the first,
although not necessarily from the same apparent sender. The Spoof Email ...
Dear
PayPal user,
We recently reviewed your account, and suspect that your PayPal
account may have been accessed by an unauthorized third party. Protecting the
security
of your account and of the PayPal network is our primary concern.
Therefore, as a prevention measure, we have temporarely limited access to
sensitive PayPal account features.
Please click on the link below to confirm your information:
https://www.paypal.com/fraudcheck/secure/bill.html?sl=070304
For more information about how to protect
your account, please visit PayPal's Security Center, accessible via the "Security Center" link
located
at the bottom of each page of the PayPal website.
We apologize for any inconvenience this may cause, and appreciate
your assistance in helping us maintain the integrity of the entire PayPal
system. Thank you for your prompt attention to this matter.
Sincerely,
The PayPal Team
Please do not reply to this e-mail. Mail
sent to this address cannot be answered. For assistance, log in to your PayPal
account and choose the "Help" link in the header of any page.
The
bogus web page ... 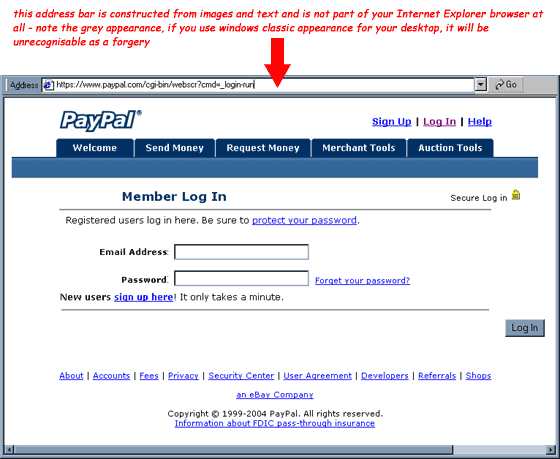
|


