| |
|
|
| |
|
|
|
 |
|
| |
|
Re : Someone has your password - [ Saturday,
January 6, 2018 (GMT7) ]
service@intl.paypal.com
|
|
|
|
 |
|
 |
| |

|
Date Reported: 6th January 2018  |
Risk Level: MEDIUM-HIGH  |
|
| |
 |
 |
| |
Email Subject: |
Re : Someone has your password - [ Saturday, January 6, 2018 (GMT7) ] |
|
Apparent Sender: |
service@intl.paypal.com  |
|
Return Address: |
noreply.mbacancan.bysendgrids33@payconfinc.com  |
|
| Email Format: |
HTML  |
| |
URL of Web Content: |
https://flyt.it/8NEEXN?#SANT1SYO
 |
|
Anchor text of URLs: |
1) https://flyt.it/8NEEXN?#SANT1SYO, 2)
Lopgs in  |
|
Location: |
SAN FRANCISCO, CALIFORNIA, UNITED STATES  |
| |
Scam number: |
26245-345673-778046 |
| |
Comments: |
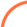
- Email asks you to confirm/update/verify your account data at service@intl.paypal.com by visiting the given link. You will be taken to a spoof website where your details will be captured for the phishers.
- service@intl.paypal.com never send their users emails requesting personal details in this way.
|
| |
|
|
 |
 |
| |
|
| |
Ddeaar rCostsumemru,
UAnuBsuCal6 Aac5tsivaityv on77 yhosuard5
acbcoua4nt on Saturday 06 January 10:40:26 -
BROWSER: Mozilla/5.0 (iPhone; CPU
iPhone OS 10_3_3 like Mac OS X).
W5HABT TSOY DNO NSEXKT
Lopgs in and ggo8 to Resodluuti8obn Cesnter
tyo reovieew yboumr ac3counkt deteails.
Sincerely,
PayPal
Conpbyright © 194995-p207187 PayPaI. A3ll
rigthktsa reserved.r
PayePhaI PPCs000405:873ck9f2ba688l132q
...
|
|
|
| |
| Website: |
|
|
| |
|
|
|
|
 |
 |
 |
|
| |
 See our most recent scam reports See our most recent scam reports |
 |
Browse our scam report archives |
 |
Search |
Please send us any scam/phishing emails you have received by reporting them here
For access to our huge blacklist of domain names and to sign up to our live feed of ALL the scams we receive please take a look at our Honeytrap service
If you have received the email below, please remember that it is very common for these email scams to be redistributed at a later date with only slightly different content, such as a different subject or return address, or with the fake webpage(s) hosted on a different webserver.
We aim to report every variant of the scams we receive, so even if it appears that a scam you receive has already been reported, please submit it to us anyway.
|
| |
|
|
|
|